If you forgot your iTunes backup password, then you can't access to your backup. iSeePassword iTunes Password Recovery is a newly released product which can help recover your backup password without damaging your original backup data. It's easy to use and works very fast.
Now, let's have a look how it works. You can directly download trail version and have a try.
Tutorial: 4 Steps to Decrypt Your iTunes Backup Password
1 Install and Run the Program on Your PC
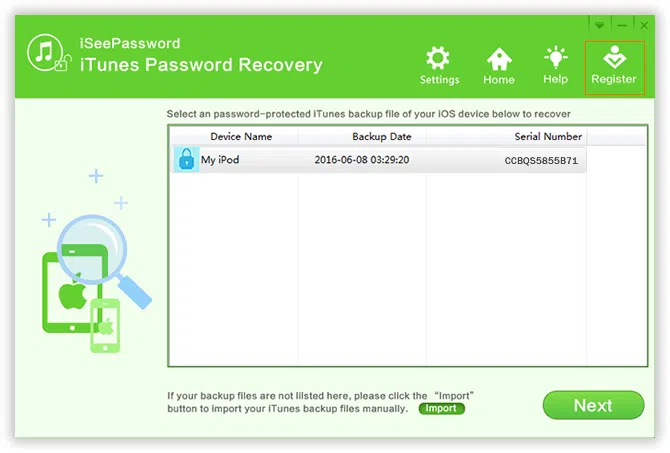
Firstly, you should download and install the program on your computer (Windows OS), run it. After the program opens, you will go to the main window below. As you can see. It will detect and load your local backup files automatically. If the program can't detect your backup files, you may need to click 'Import' button to import your backup file manually.
NOTE: This is manifest.plist file. The default path where this backup file is stored varies in each windows system.
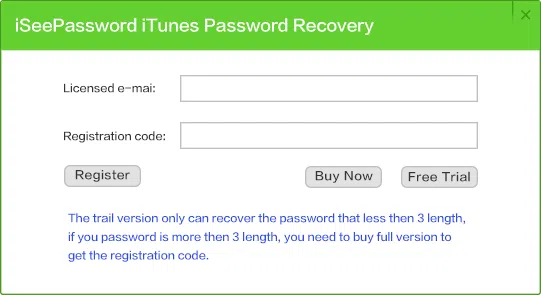
2 Register the Program
The trail version only can unlock the password length that less than 3 characters, if your password length is more than 3, then you will be asked to register the program. To register the program, just click 'Register' the button in the top right corner and type the email and code.
Email: this is your purchase email, you typed in the purchase form.
Registration Code: When you purchased program, you should receive an email with code included.
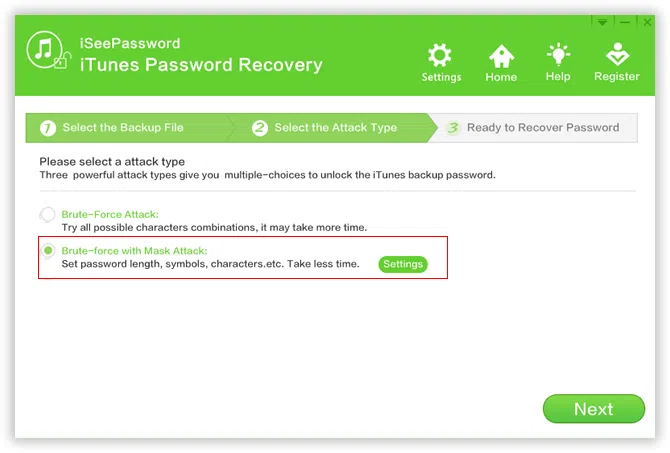
3Select the Appropriate Attack Type
To get back your password in the shortest time, there are current 2 attack types built in the program target to different purpose, - "Brute-force Attack", "Mask Attack", each attack type has different requirements, so you need to select the most appropriate types in the drop menus of "Type of attack" to effectively decrypt your iTunes backup.
Brute-force Attack: If you can't remember any bit of information of your password, you have to select this attack type, it will try all possible characters combination in the specified Range you have set, however, this may take relatively longer time than the other types.
Brute-force with Mask Attack (highly recommended):
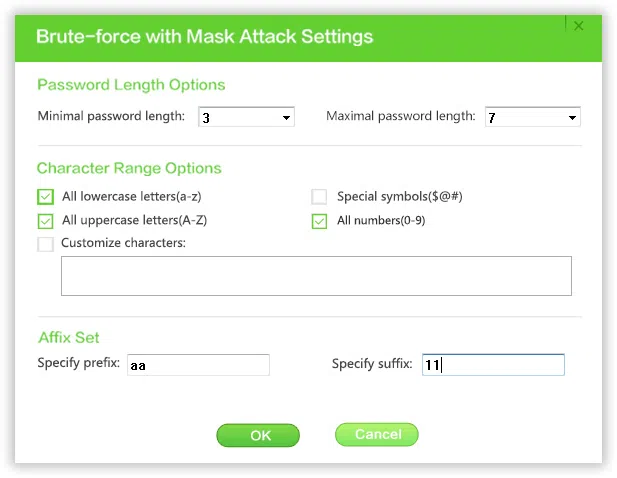
It is highly recommend using this attack type if you still remember part of your password like length, characters. For example, if you remember your password length is 5 characters and begins from "T" ,
Minimal Length: Set a minimal password length.
Maximal length: Set a maximal password length.
Character Range Options: What kind of characters does your password includes or not, then check the box in "character range option".
Customize Characters: If you check this option, then you should type all possible characters of your password. For example, Maybe you think your passwords includes: T, Z, A, 1,2,3,4,5,6, S, w, d,y,h,k. Then you can type these characters in the Customize form. The program only search all the combinations of these characters. This can be used in conjunction with specify prefix and specify suffix.
Affix Set: If you remember the first or last character of your password, then you can specify prefix or suffix, this will scan your password quickly.
See how to use Mask Attack Settings:
4Begin to Decrypt Password-Protected iTunes Backup
When everything is OK, click "Start" to start decrypting backup files, it will take some times based on the password information you provide, such as length, characters,etc. The more detailed information you provide, the faster the process will get done.
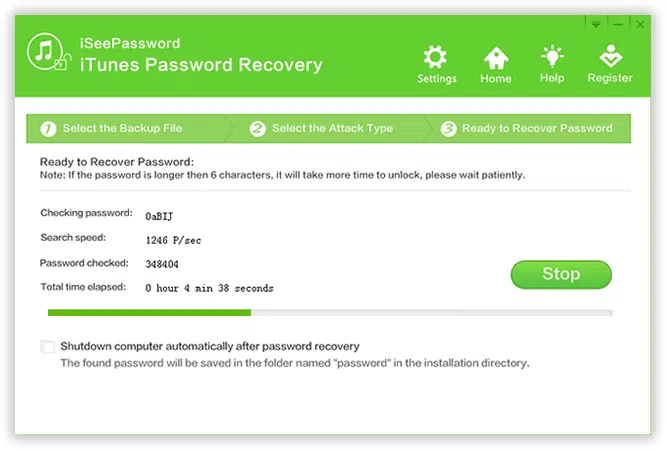
Stop/Save: You can directly click the "Stop" button to pause the process, then click "Save" the project for next use, this allows you to import previous results to the program for resuming the process without re-scanning.
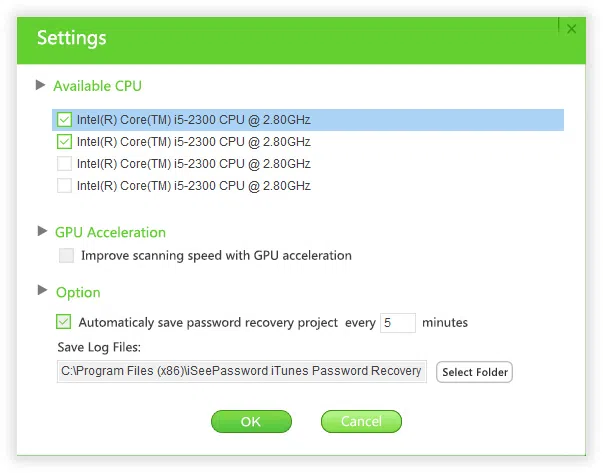
Pause/ Resume: You can click to 'Pause' button to pause the searching, then click 'Settings' to select 'CPU' or 'GPU'. Then click 'Resume' to continue searching.
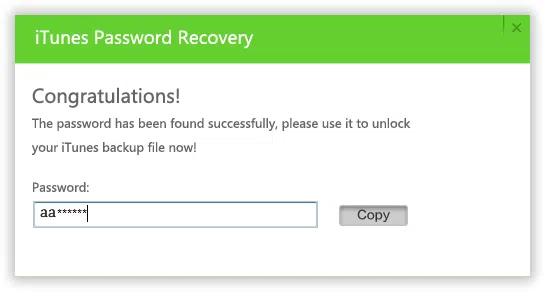
When the program start to scanning, it may take some times depend how complex your password is, so just wait patiently. Once the program finds your password, a windows will pop up saying "Congratulation! The password has been found". Just click the copy button and paste it to a text or .doc.
NOTE:
1) When you select 'Showdown computer', then you can leave your computer running all the time, once your password is found, the password will be saved as .Text in the program installation path.
2) It will take long time if the password is more than 8 length, or take longer time (hours, days or weeks) based on the password complexity and length. So be patient.
3) The program searching speed is absolutely faster then competitors' product. To increase the searching speed, you need to improve computer's performance like CPU and GPU.
Related Articles & Tips