If you are used to exchanging a lot of data, like documents, images, audios, videos, movies frequently with family and friends, then the use of flash drive or USB Drive must be a great help to you. Indeed, it has rendered the conveyance of data from one computer to another without any internet connection possible. But at the same time, it has paved way to risks of data being copied for unfair means.
- Method 1: Protect USB Drive from Being Copied with USB Copy Protection
- Method 2: Protect USB Drive using USB Locker Tool
If you leave your USB drive unprotected here and there on your working table or elsewhere, you are most likely to come under the risk that any intruder might grab it to access and copy your contents. Thus it is of paramount importance to safeguard the contents of the USB for your personal safety as it can contain confidential details, which you would definitely not wish to share with anyone else.
Now the question arises, how come you accomplish the task of protecting USB from copied? Well that’s why we are here to help you know what steps and measures can be undertaken to do the job of USB protection. Here in this article we would mentioned two popular USB copy protection tools which would perform the job of data security.
[ps2id id=’Method-1′ target=”/]Method #1: Protect USB Drive from Being Copied with USB Copy Protection
USB Copy Protection Tool is one of the most popular USB security tool which has in the recent times has gained a lot of fame because of its stupendous performance.
Step 1. Download USB Copy Protection and run the setup after installation.
Step 2. Insert your USB stick to the computer port, and assume that there are many data in your USB drive. After launching the program, from the main screen, select the USB disk that you wish to protect.
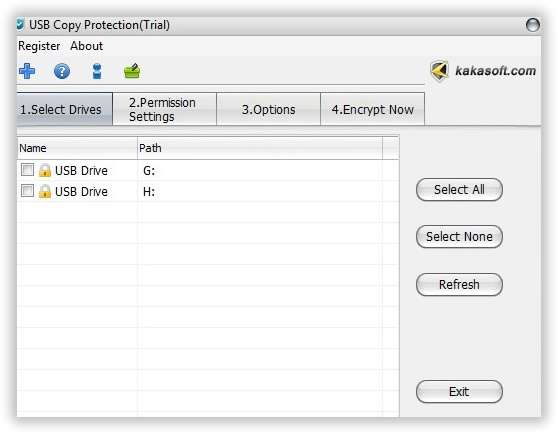
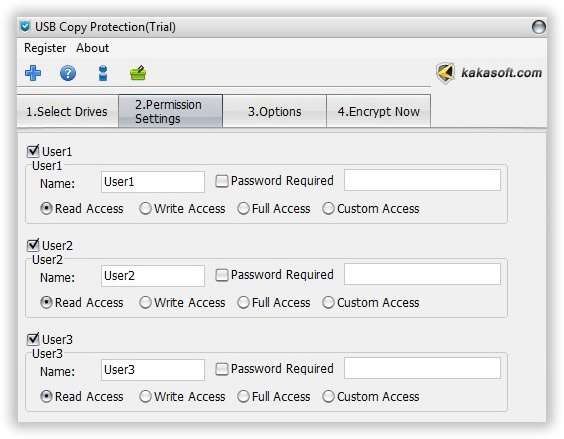
Step 3. Go to the “Permission Settings” panel where you can set the restrictions for the users to use the USB drive and its contents. For instance, Read Access, Write Access, Full Access, Custom Access options allows the user to restrict the read and write privileges as per your requirement.
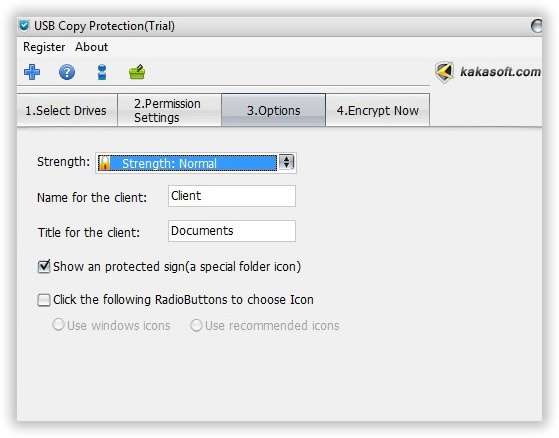
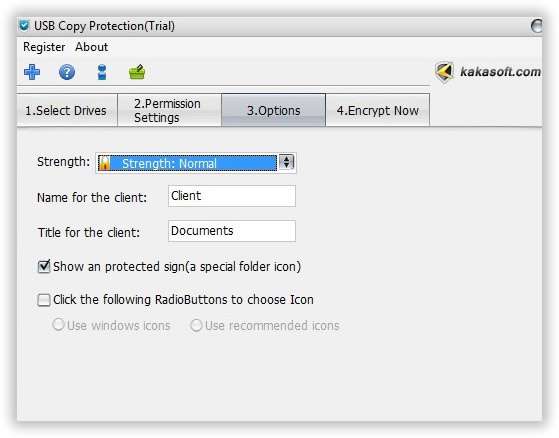
Step 4. Now go to the “Options” section and set the suitable protection strength according to the risk you are so dreading.
Step 7. Navigate to the “Encrypt Now” panel and enter your admin password or the password “123456” if you are currently using the trial version of the tool.
Step 8. Click “Protect” button to start protect your USB from bed copied. Now; once the USB drive is protected it can only be assessed by entering the mentioned password to access the contents within the drive.
[ps2id id=’Method-2′ target=”/]Method #2: Protect USB Drive using USB Locker Tool
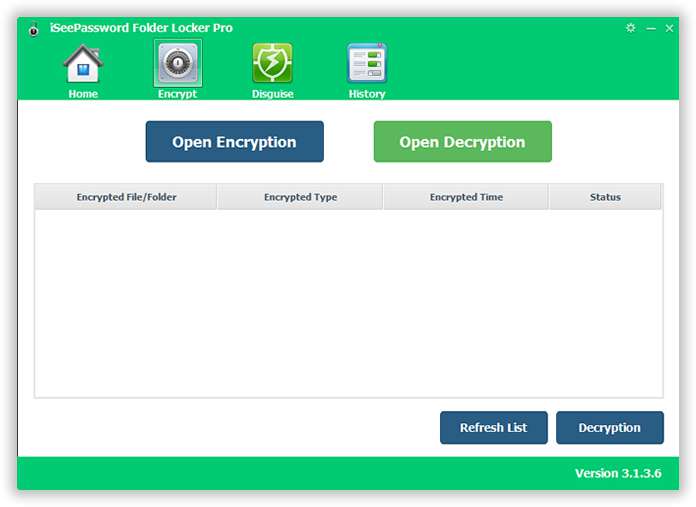
iSeePassword Folder Locker Pro is a wonderful USB Protection tool which can be used to password protect USB drive, file, folder and memory card and other devices. One the of interesting function is that it can keep file, folder, USB in disguise mode by changing their icons and their appearance, strangers will be misdirected. But here in this topic we would restrict the discussion only up to the USB protection only. The steps to use the tool are explained as follows:
Step 1. Firstly download the program from its official website, and run the program file to install the tool.
Step 2. Now after the installation is done, insert your USB stick into the computer port.
Step 3. Select your USB drive and you will be asked to set the size of the encryption area. Click “Install” to set the password.
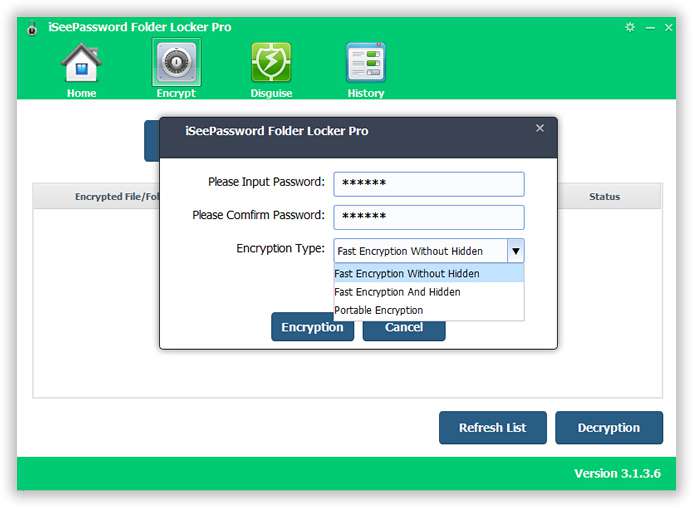
Step 4. Enter your password and press “Ok” to apply for the changes from the pop-up menu that appears. Once the USB protection encryption is done, click “Ok” button to finish the process.
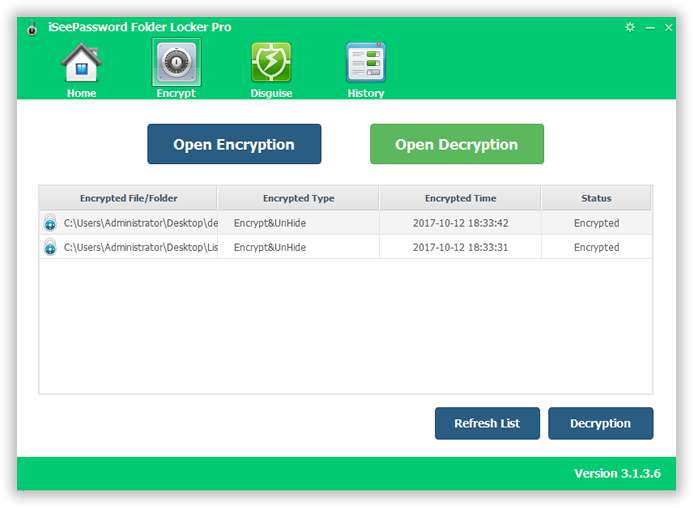
Step 6. Now open the same USB drive in your computer, you also will find the files, folders in yourUSB are hidden, but this time you will be asked to enter the password. This indicates the password protection has been set right.
Conclusion:
Data is the most crucial aspect in today’s generation, and thus securing the data can ensure safety of the user from various perspectives. And when it is about the USB drive which is more vulnerable to exploitation because of its easier assessment, it becomes much more important for the user to safeguard the contents of the USB from misuse. The methods mentioned above in this article can be pulled off by anyone knowing the basic know-how of computer.
Related Articles: